For large and fast-growing development teams
Deliver a better product experience with code monitoring at scale
Increase developer velocity and remove silos with full visibility into your code health across your frontend, backend, APIs, and microservices — in a single platform.
Get in touchHelp developers see clearer, solve quicker, and learn continuously

See issues that really matter
Visibility across all platforms, so no bug gets away from you.

Solve issues in minutes
Deep context removes back-and-forth issue remediation across teams.
Learn insights to improve
Uncover trends and anomalies across your projects, teams, and organization.
We scale with you
Every part of Sentry is designed with high availability and redundancy in mind.
When your events spike, we'll be ready.
85k
Organizations seeing clearer
235k+
Products and services monitored
3.5M+
Developers solving issues faster
790B
Events recieved each month
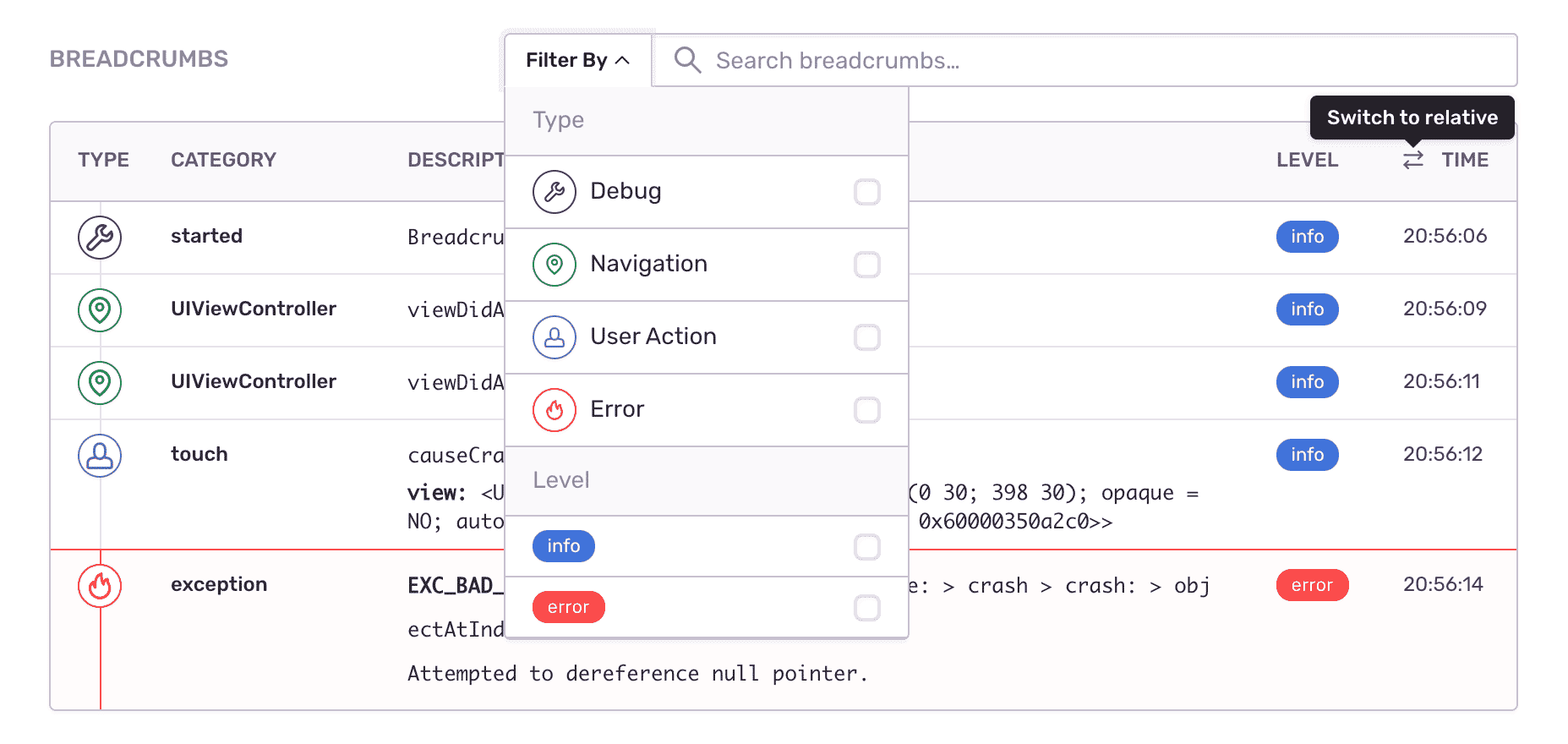
Accelerate time to resolution with deep issue context
Quickly pinpoint when, where, and why a user experiences an issue–and who owns the broken code–with actionable error details like the commit that introduced the error, the code owner, and the user actions and functions leading up to when it occurred, so you can reproduce and fix issues faster.
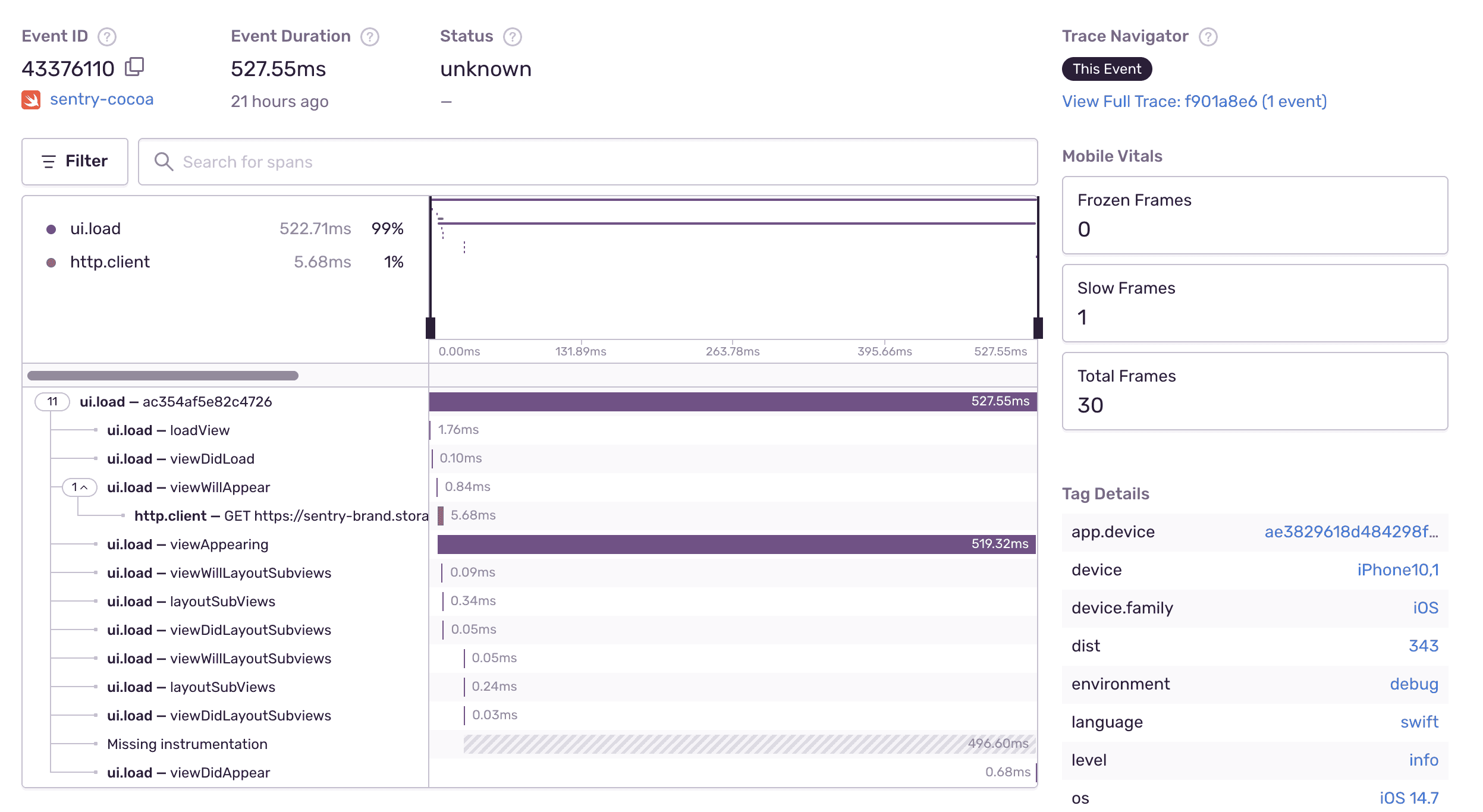
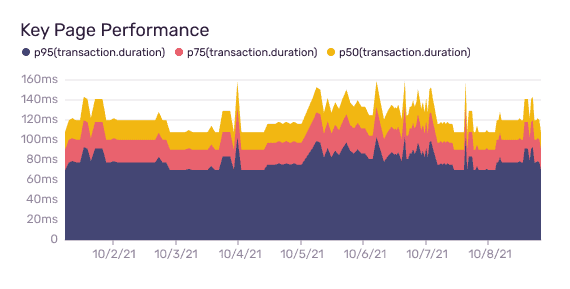
See slow faster with performance monitoring
Stop querying log files to troubleshoot performance issues. Use Sentry Tracing to quickly identify errors and latency problems by tracing from your frontend through all your services to see the exact poor-performing API call or slow database query.
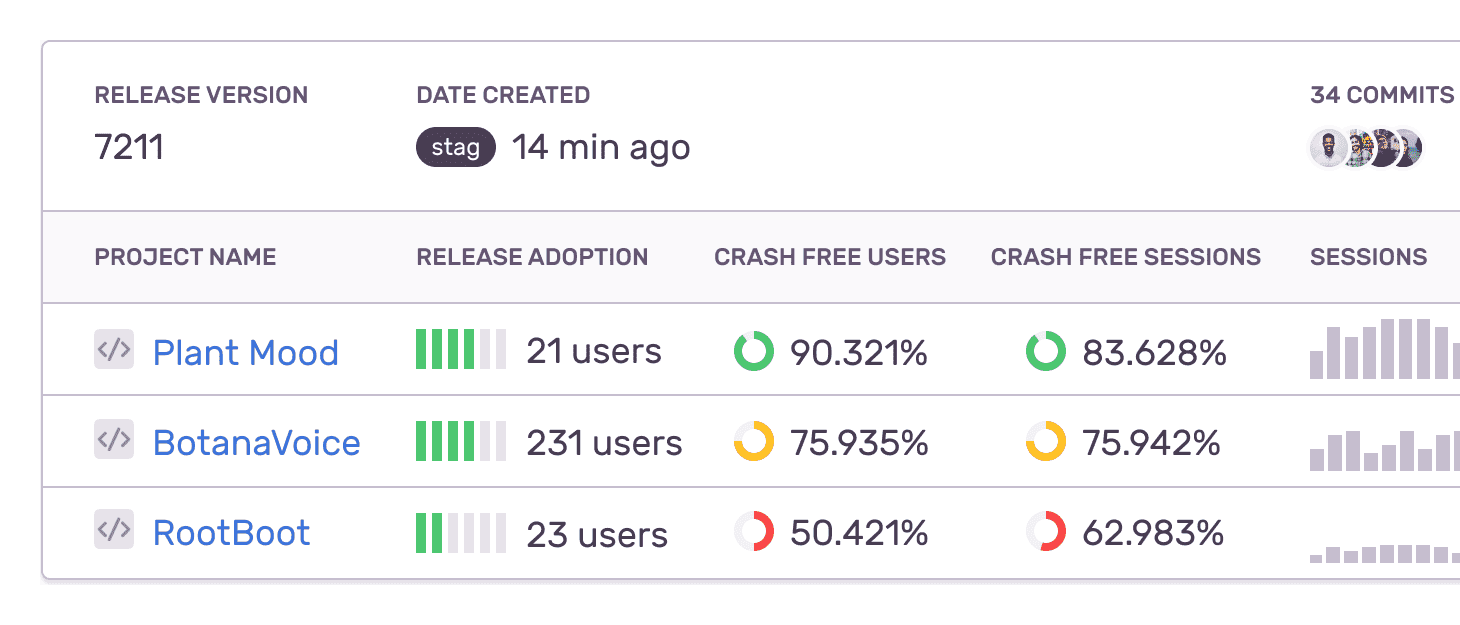
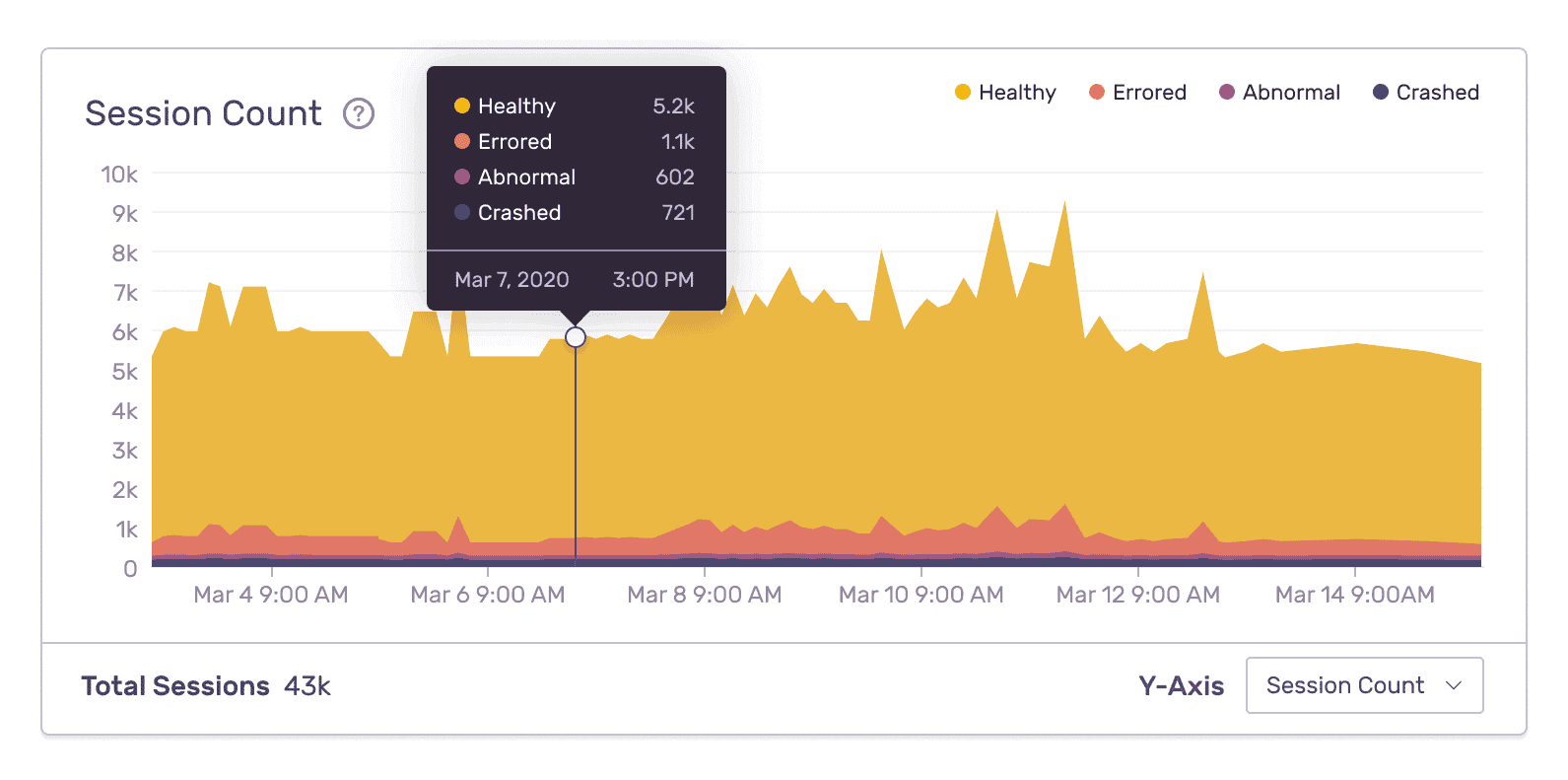
Maintain quality and stability with Release Health
Get real-time visibility across releases to see core metrics like crash-free sessions, version adoption, and failure rate so you can see the moment a release starts to degrade and quickly take action.
Uncover business insights with custom queries and dashboards
Identify historical trends and anomalies to optimize code health across your projects and teams. With Sentry’s visual query builder you can query against cross-environment error, release, and application performance data so you can get a holistic view into the health of your entire system.
Reduce operational overhead
Streamline your workflow to optimize the developer and customer experience with 45+ out-of-the-box tools and an open API to build custom integrations. Developers can receive alerts and the context they need to take action faster in the tools they use every day.
Your business is our business
When all hell breaks loose, we're here to help.
Scalable user management and compliance
With single sign-on, SAML, SCIM support, and audit trails, all Sentry customers have access to admin controls that govern identity, access, and usage to keep your data safe, secure, and centrally managed.
Automatic and Continuous improvement
Don't leave yourself vulnerable with an outdated instance. While we deploy to production multiple times a day, Sentry is always up-to-date (without you even lifting a finger).
Support
Build a code observability practice customized to your organization. With a dedicated support team, you can discuss product questions, get onboarding help, and provide product feedback almost instantly.
Reliability
We strive to always be available — Sentry rarely encounters issues. Check for yourself at status.sentry.io, our transparent dashboard that tracks our uptime in real time.

Exceed security and privacy requirements
Security and compliance are top priorities for Sentry because they are fundamental to your experience. We use a variety of industry-standard technologies and services to secure your data from unauthorized access, disclosure, use, and loss. We undergo a security penetration test from an independent, third-party agency, and we are GDPR, HIPAA, ISO27001, and SOC2 Type 2 compliant as well as Data Privacy Framework certified.
Learn more




”Sentry's high-quality tooling helps Disney+ maintain high-quality service to its tens of millions of global subscribers.”

A peek at your privacy
Here’s a quick look at how Sentry handles your personal information (PII).
×Who we collect PII from
We collect PII about people browsing our website, users of the Sentry service, prospective customers, and people who otherwise interact with us.
What if my PII is included in data sent to Sentry by a Sentry customer (e.g., someone using Sentry to monitor their app)? In this case you have to contact the Sentry customer (e.g., the maker of the app). We do not control the data that is sent to us through the Sentry service for the purposes of application monitoring.
Am I included?PII we may collect about you
- PII provided by you and related to your
- Account, profile, and login
- Requests and inquiries
- Purchases
- PII collected from your device and usage
- PII collected from third parties (e.g., social media)
How we use your PII
- To operate our site and service
- To protect and improve our site and service
- To provide customer care and support
- To communicate with you
- For other purposes (that we inform you of at collection)
Third parties who receive your PII
We may disclose your PII to the following type of recipients:
- Subsidiaries and other affiliates
- Service providers
- Partners (go-to-market, analytics)
- Third-party platforms (when you connect them to our service)
- Governmental authorities (where necessary)
- An actual or potential buyer
We use cookies (but not for advertising)
- We do not use advertising or targeting cookies
- We use necessary cookies to run and improve our site and service
- You can disable cookies but this can impact your use or access to certain parts of our site and service
Know your rights
You may have the following rights related to your PII:
- Access, correct, and update
- Object to or restrict processing
- Port over
- Opt-out of marketing
- Be forgotten by Sentry
- Withdraw your consent
- Complain about us
If you have any questions or concerns about your privacy at Sentry, please email us at compliance@sentry.io.
If you are a California resident, see our Supplemental notice.